作用
- 主要是在最近使用的项目需要使用
RestfulApi,然后现在需要使用C#来操作,周末看了一些帖子,最后发现很多都是错误的,最后跑通了做记录。
基本代码
- 安装需要的包
- 配置
appsettings.json,主要是后面jwt的节点信息。
{
"Logging": {
"LogLevel": {
"Default": "Information",
"Microsoft.AspNetCore": "Warning"
}
},
"AllowedHosts": "*",
"Jwt": {
"SecretKey": "67752d310d8c407793a453f1709a9738",
"Issuer": "WebAppIssuer",
"Audience": "WebAppAudience",
"ExpireTime": 60
}
}
var configuration = builder.Configuration;
builder.Services.AddSingleton(new JwtHelper(configuration));
builder.Services.AddAuthentication(options =>
{
options.DefaultScheme = JwtBearerDefaults.AuthenticationScheme;
})
.AddJwtBearer(options =>
{
options.TokenValidationParameters = new TokenValidationParameters()
{
ValidateIssuer = true,
ValidIssuer = configuration["Jwt:Issuer"],
ValidateAudience = true,
ValidAudience = configuration["Jwt:Audience"],
ValidateIssuerSigningKey = true,
IssuerSigningKey = new SymmetricSecurityKey(Encoding.UTF8.GetBytes(configuration["Jwt:SecretKey"])),
ValidateLifetime = true,
ClockSkew = TimeSpan.FromSeconds(30),
RequireExpirationTime = true,
};
});
builder.Services.AddSwaggerGen(c =>
{
c.SwaggerDoc("v1", new OpenApiInfo { Title = "WebAPI", Version = "v1" });
var securityScheme = new OpenApiSecurityScheme
{
Name = "JWT Authentication",
Description = "Enter JWT Bearer token **_only_**",
In = ParameterLocation.Header,
Type = SecuritySchemeType.Http,
Scheme = "bearer",
BearerFormat = "JWT",
Reference = new OpenApiReference
{
Id = JwtBearerDefaults.AuthenticationScheme,
Type = ReferenceType.SecurityScheme
}
};
c.AddSecurityDefinition(securityScheme.Reference.Id, securityScheme);
c.AddSecurityRequirement(new OpenApiSecurityRequirement
{
{ securityScheme, new string[] { } }
});
});
app.UseAuthentication();
app.UseAuthorization();
public class AuthenticationBaseInfo
{
[NotNull]
public string? ClaimName { get; set; }
[NotNull]
public string? ClaimRole { get; set; }
[NotNull]
public string? UserName { get; set; }
[NotNull]
public string? Name { get; set; }
public AuthenticationBaseInfo(string? claimName = default, string? claimRole = default, string? userName = default, string? name = default)
{
ClaimName ??= claimName;
ClaimRole ??= claimRole;
UserName ??= userName;
Name ??= name;
}
}
using Microsoft.IdentityModel.Tokens;
using System.IdentityModel.Tokens.Jwt;
using System.Security.Claims;
using System.Text;
namespace AuthenticationTest;
public class JwtHelper
{
private readonly IConfiguration _configuration;
public JwtHelper(IConfiguration configuration)
{
_configuration = configuration;
}
public void CreateToken(AuthenticationBaseInfo authenticationBaseInfo, out string token, out DateTime expirationTime)
{
token = string.Empty;
expirationTime = DateTime.Now;
if (authenticationBaseInfo == null)
{
return;
}
var cliamns = new[]
{
new Claim(ClaimTypes.Name, authenticationBaseInfo.ClaimName),
new Claim(ClaimTypes.Role, authenticationBaseInfo.ClaimRole),
new Claim(JwtRegisteredClaimNames.Jti, authenticationBaseInfo.ClaimRole),
new Claim("UserName",authenticationBaseInfo.UserName),
new Claim("Name",authenticationBaseInfo.Name),
};
var secretKey = new SymmetricSecurityKey(Encoding.UTF8.GetBytes(_configuration["Jwt:SecretKey"]));
var algorithm = SecurityAlgorithms.HmacSha256;
var signingCredentials = new SigningCredentials(secretKey, algorithm);
var jwtSecurityToken = new JwtSecurityToken(
_configuration["Jwt:Issuer"],
_configuration["Jwt:Audience"],
claims,
DateTime.Now,
DateTime.Now.AddMinutes(30),
signingCredentials
);
token = new JwtSecurityTokenHandler().WriteToken(jwtSecurityToken);
expirationTime = jwtToken.ValidTo;
}
}
- 需要注意的一点是,这里加密算法选择的
SecurityAlgorithms.HmacSha256,所以需要的密钥长度是256bit,也就是32长度的字符,所以appsettings.json里面的SecretKey长度为32位,不然会报错。(反正我测试的时候少于32是报错的,要是不正确的话可以联系修改)。
- 建立一个
UserController,代码如下.
[Route("api/[controller]/[action]")]
[ApiController]
public class UserController : ControllerBase
{
private readonly JwtHelper _jwtHelper;
public UserController(JwtHelper jwtHelper)
{
_jwtHelper = jwtHelper;
}
[HttpPost]
public string GetToken()
{
AuthenticationBaseInfo authenticationBaseInfo = new AuthenticationBaseInfo()
{
UserName = "hello",
Name = "hello"
ClaimName = "admin";
ClaimRole = "admin";
};
jwtHelper.CreateToken(authenticationBaseInfo, out var token, out var expirationTime);
if (!string.IsNullOrWhiteSpace(token))
{
return Ok(token);
}
else
{
return BadRequest("账号或密码错误!");
}
}
[HttpGet("hello")]
[Authorize(Roles = "admin")]
public string Hello()
{
return "Hello";
}
}
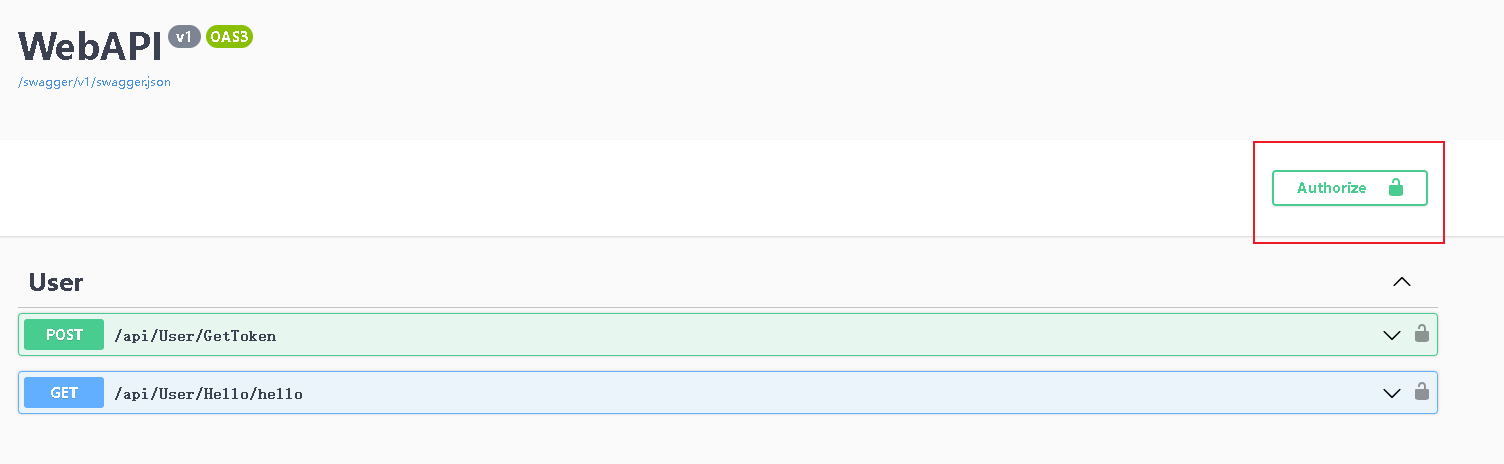
- 在网页的
swagger上,可以看到有锁的样子。
 )
)
- 首先使用第一个的
Post中返回的token,然后填入到红线显示的里面,注意有的博客说的是前面需要加上Bearer 的前缀,但是我检验发现其实是不需要添加的。
- 后续的操作跟其余的控制器一样。
注意
- 在使用的时候其实还是有一些问题的,例如其实返回应该使用
ActionResult,在授权的时候其实应该添加根据Role的筛选的。
- 服务注册是一个很有用也很有意思的一个功能,我之前了解的不是很深,所以后续这一块我打算再认真学一下,后续项目中打算以这个作为一个提升方向。
- 感觉
C#这个Web端有时候还是有点麻烦。这个项目多多少少我接触的不多估计会有很多bug,争取在今年年底能有一个初步的软件规模。
 )
)